How to install on premises with docker compose
Deployment
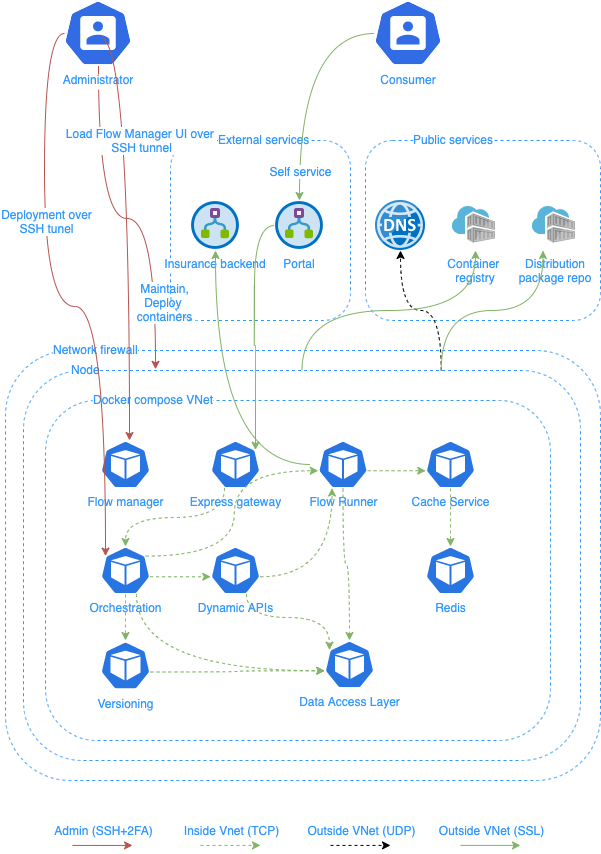
Prerequisites
While ACE can run on various Linux distributions. This guide is how to install it on Ubuntu LTS (20.04) or CentOS 8.
- Server with SSH access enabled
- Outbound Internet access
- Docker installed
- Docker-compose installed
Docker installation
- Ubuntu
- CentOS
sudo apt-get update
sudo apt-get install \
apt-transport-https \
ca-certificates \
curl \
gnupg \
lsb-release
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /usr/share/keyrings/docker-archive-keyring.gpg
echo \
"deb [arch=amd64 signed-by=/usr/share/keyrings/docker-archive-keyring.gpg] https://download.docker.com/linux/ubuntu \
$(lsb_release -cs) stable" | sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt-get update
sudo apt-get install docker-ce docker-ce-cli containerd.io
sudo yum install -y yum-utils
sudo yum-config-manager \
--add-repo \
https://download.docker.com/linux/centos/docker-ce.repo
sudo yum install docker-ce docker-ce-cli containerd.io
sudo systemctl start docker
Manage Docker as a non-root user
The Docker daemon binds to a Unix socket instead of a TCP port. By default that Unix socket is owned by the user root and other users can only access it using sudo. The Docker daemon always runs as the root user.
If you don’t want to preface the docker command with sudo, create a Unix group called docker and add users to it. When the Docker daemon starts, it creates a Unix socket accessible by members of the docker group.
sudo groupadd docker
sudo usermod -aG docker $USER
newgrp docker
Configure Docker to start on boot
sudo systemctl enable docker.service
sudo systemctl enable containerd.service
Docker Compose installation
sudo curl -L "https://github.com/docker/compose/releases/download/1.29.2/docker-compose-$(uname -s)-$(uname -m)" -o /usr/local/bin/docker-compose
sudo chmod +x /usr/local/bin/docker-compose
Two factor authentication
On production environment we recommend to set up 2FA. Here is guide how to deploy two factor authentication.
Keys
On production environment we recommend to configure SSH key-based authentication.
Network security
Machine running ACE must implement network level security to allow only incoming traffic on ports 22 (Admin) and 443 (API Gateway).
Deploy ACE
# authentication for users with credentials
docker login euadigportalcoredev02acr.azurecr.io
curl -sS -0 "https://dev.ace-community.sapienspaas.com/release/ace4-docker-compose.yml" -o "docker-compose.yml"
docker-compose up
If you want to run ACE in the background, you can pass the -d flag (for "detached" mode) to docker-compose up and use docker-compose ps to see what is currently running:
docker-compose up -d
If you started ACE with docker-compose up -d, stop your services once you’ve finished with them:
docker-compose stop
You can bring everything down, removing the containers entirely, with the down command:
docker-compose down
Work with ACE
To work with ACE user interface on production environment we recommend using SSH Port Forwarding (SSH Tunneling).
ssh -L 8080:localhost:5005 -L 3000:localhost:3000 user@server
Once SSH tunnel is created, open ACE Manager to access ACE user interface.