Securing Dynamic APIs
Secured API feature is disabled since ACE 4.39 version
Recommended way to secure Dynamic API's is described in Security page.
Approach below requires to configure ACE orchestration service and each individual API.
Configuring API
By default, APIs are available anonymously, and to turn on authentication it's necessary to check Secured option on Dynamic API screen.
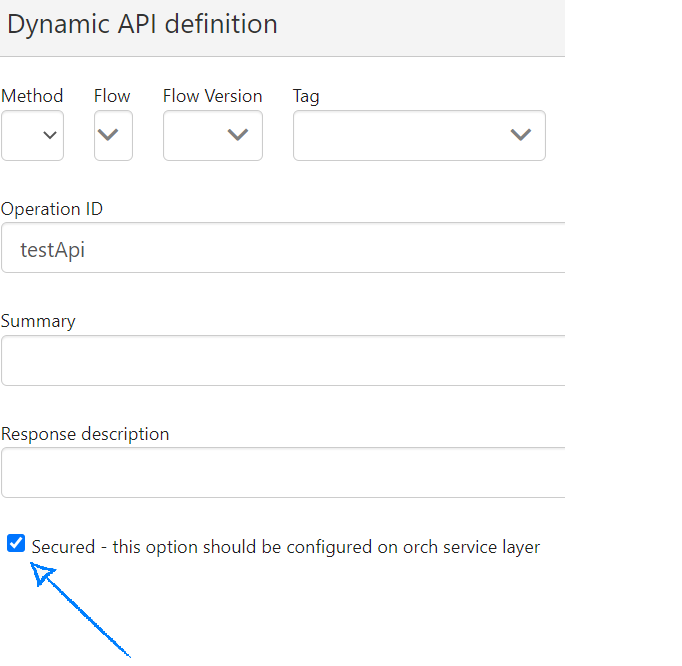
After this follow below steps to configure orchestration layer
Configuring Orchestration layer
It's necessary to provide following environmental variables in Orchestration layer for authentication to work
DYNAMIC_API_AUTH_STRATEGY- possible valuebearerDYNAMIC_API_KEYCLOAK_REALM- Keycloak realmDYNAMIC_API_KEYCLOAK_AUTH_SERVER_URL- Keycloak server URL, for examplehttps://keycloak.mysite.com
For Keycloak under 17 auth url should have /auth suffix.
Example configuration:
DYNAMIC_API_AUTH_STRATEGY=bearer
DYNAMIC_API_KEYCLOAK_AUTH_SERVER_URL=http://localhost:8282
DYNAMIC_API_KEYCLOAK_REALM=ACE
Restart the orch service after these env configs are set.
How to test secured api feature.
It's typical to have CORS configuration issue, please check if authorization header and Keycloak host is enabled in CORS headers.
Step 1: Select the secured api you want to execute. You will see Authorize button when api is expaned.
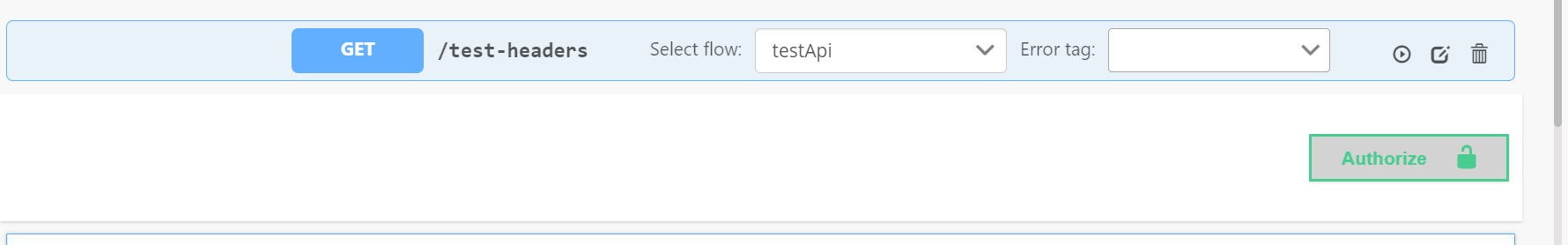
Step 2: Click on the Authorize button and popup will open. Enter the access token generated from the keyclock server. Press enter and then close the popup.
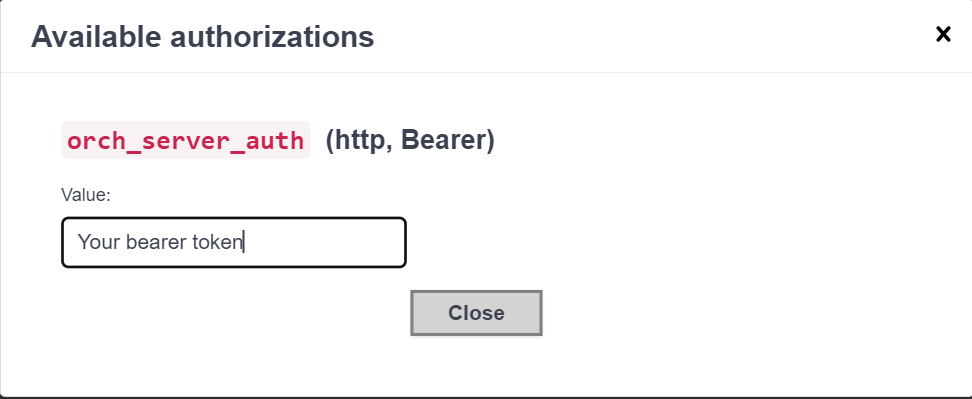
Please see this documentation to learn how to generate token from Keycloak server. Keycloak User token
Step 3. Execute api as usual and in the curl command you should see the token is passed in Authorization header.
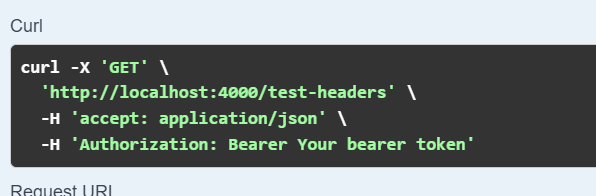
The api will be successful if the access token is valid and otherwise api will fail with 401 status code.